This is a small tool to set environment variables from encrypted (with GPG) files
There are many command line tools that require environment variables with secret values to work. These values are often saved in unencrypted shell files. I created this simple but useful script to read secret values from encrypted files and at the same time make it easy to login in and out from diferent accounts.
NOTICE: GPG is assumed to be installed and configured for the current user.
Copy the shell-secrets.sh file anywhere in your disk. Add the following line in your profile shell script:
Also is recommended to modify the shell prompt to display the current login. For example this can be inserted in your PS1 variable:
The variable $SECRET_LOGIN keeps the list of account names being used in the current shell.
First, make sure the ~/.shell-secrets/ directory exists. This is where encrypted files will be stored:
Now create new encrypted files using GPG:
Done!
To login using any of the encrypted files, just call the login function with the file name (without the .gpg extension)
The enviroment variables are set and ready to be used and the SECRET_LOGIN environment variable is updated to be used by the prompt. The script also includes autocomplete for the available file names in the .shell-secrets directory.
Several logins can also be nested:
Every time the login function is used, a new sub-shell process is created. To logout from the current account, call logout or just press Ctrl+D.

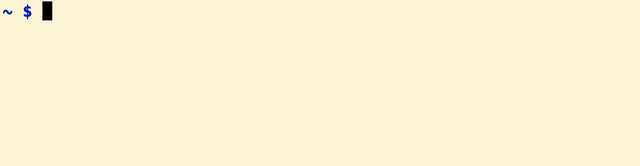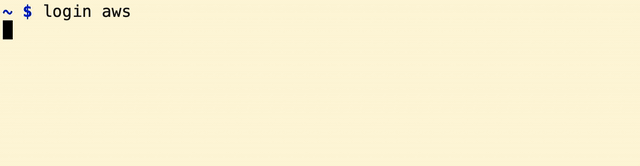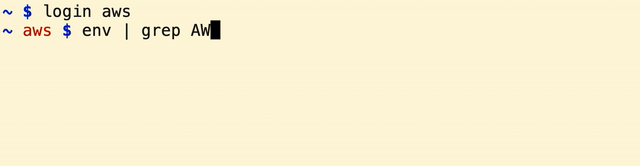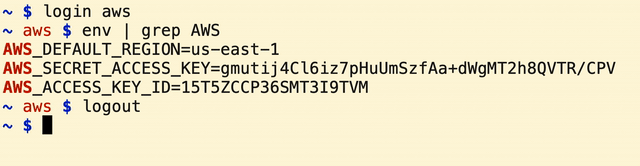






 English (US) ·
English (US) ·